MEMCM - Migration from On premise to Intune - Part 6 - Migration of Policies
Planning for Client & Endpoint Security Policies
Introduction
The last part on this series will now focus on the various policies within MEMCM, mainly the client policies and the Endpoint/Defender policies.
There is an interesting split as to how client policies can be migrated over but due to the various categories which are displayed in both policies for your MEMCM & then the profiles within Intune will make an interesting exercise to explore the overall mapping.
For Defender policies we will also dive into the migration of these policies and how they fit into a profile around the Endpoint Security area of Intune and how they will all fit overall in your Modern Workplace Management.
( Note:
When performing migrations of policies in general its best advised to testing these first on machines which your policies that are controlled on-premise to be turned off so that you able to obtain a true baseline of working policies once migrated into Intune for your Modern Workplace Management. Then once happy with the testing you can make the transition of it being controlled only by Intune
)
Client Policy Mapping
Various settings are set by default within your Default Client Settings policy in your on-premise MEMCM. So for all of the settings which are not only applicable but also can be configured within Intune will be explored even further.
The migration of these specifics are not as straight forward as the other parts in this series due to the fact that a lot of the policies have a primary focus on the on premise client settings which utilise the communications & polling methods, however there are some which provide a more overall configuration of the whole Intune/Modern Workplace Management experience.
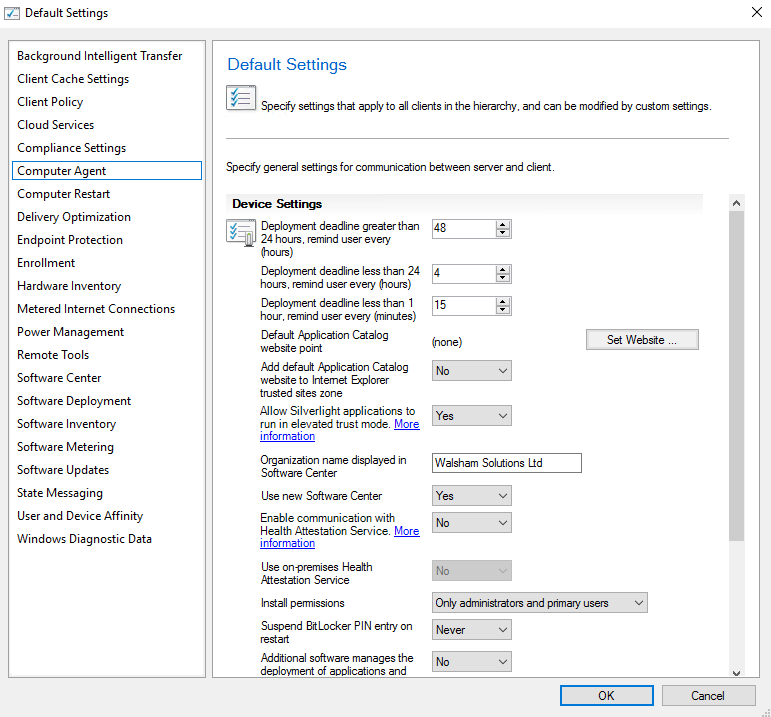
Computer Agent
The computer agent has settings specifically for your on premise SCCM.For example, if we take the Computer Agent policy as seen below in my default settings.
These settings control the overall branding of the MEMCM environment which you have. So you would expect to see these around your Software Centre & some cases your Application Catalog.
Now within your Modern Workplace Management your Software Centre
is essentially your Company Portal
whether that be the actual windows application or the web based version. Also not to mention your Auto Pilot/Enrollment/White Glove process as well. So these settings are then migrated into the Tenant Admin End User Experience Section.
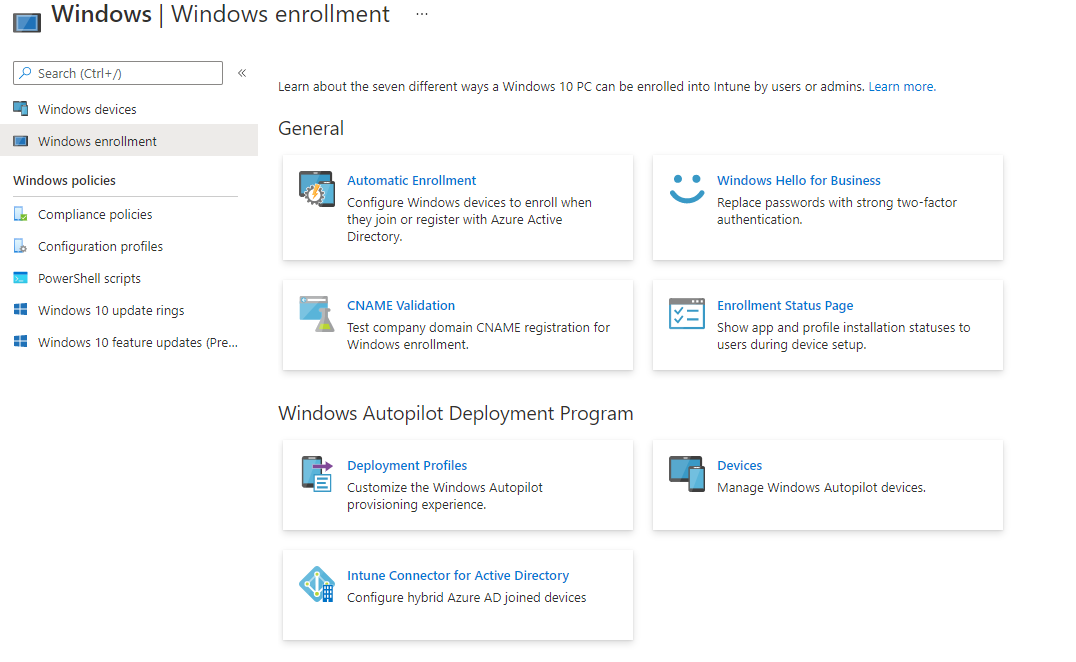
Enrollment
Where enrollment is concerned these are covered within the MDM settings, Enrollment Profile pages and also the Auto Pilot provisioning section of your Intune Device Management.
Enrollment settings of course vary from device type, where Android, iOS and MacOSX have their own enterprise level methods of enrollment where you might have a PKI topology and authentication roles defined within MEMCM if you are managing these on premise. There maybe situations in which you were an early adopter of going to the MDM when Intune was transitioning into the Intune Standalone a couple of years back.
Having said that if we look into the enrollment settings on your on premise MEMCM there are options such as allowing users to register devices, now these specific settings are a bit spread out and can be controlled within administrative permissions using RBAC (Role based access control) within your Intune Tenant admin settings.
Hardware/Software Inventory
Unlike the on premise MEMCM settings there are no policies within Intune which can actually set a polling interval to collect the information as this is done in a more hardcoded way.
When devices enroll areas such as Discovered Apps (equivalent to Software Inventory) will collection information ranging from 24 hours (win32 apps) and 7 days for all of the rest. The Hardware Inventory follows the same type of polling. Below are some ideas on how the actual inventory looks like for both hardware and software.
It is to note that the Intune Data Warehouse can also pull down the exact same kind of information for both inventories if you choose to build a custom report or Power BI dashboard from the same information.
Remote Settings
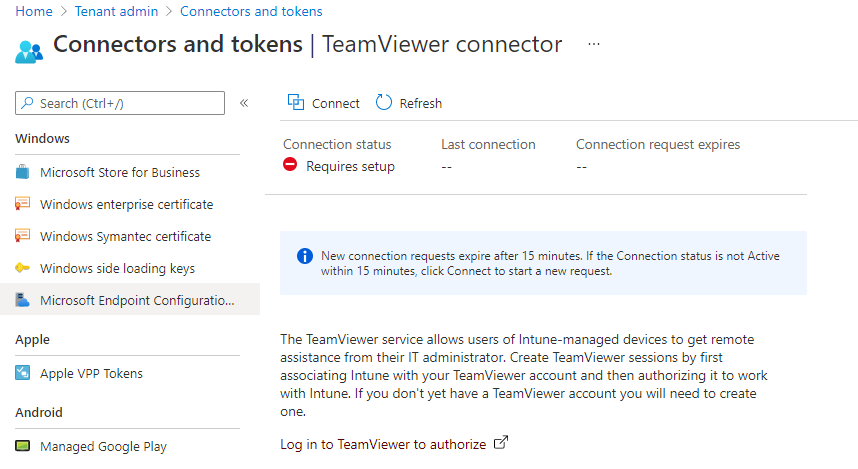
In your On Premise MEMCM you would be able to use the remote control application which will enable you to remotely connect and control a managed asset within your on premise estate.
Intune currently does not have an equivalent as such. But there is a Teamviewer connector which can integrate with your Intune Device Management and this can therefore provide the same service as well as compensate for the policy settings as well.
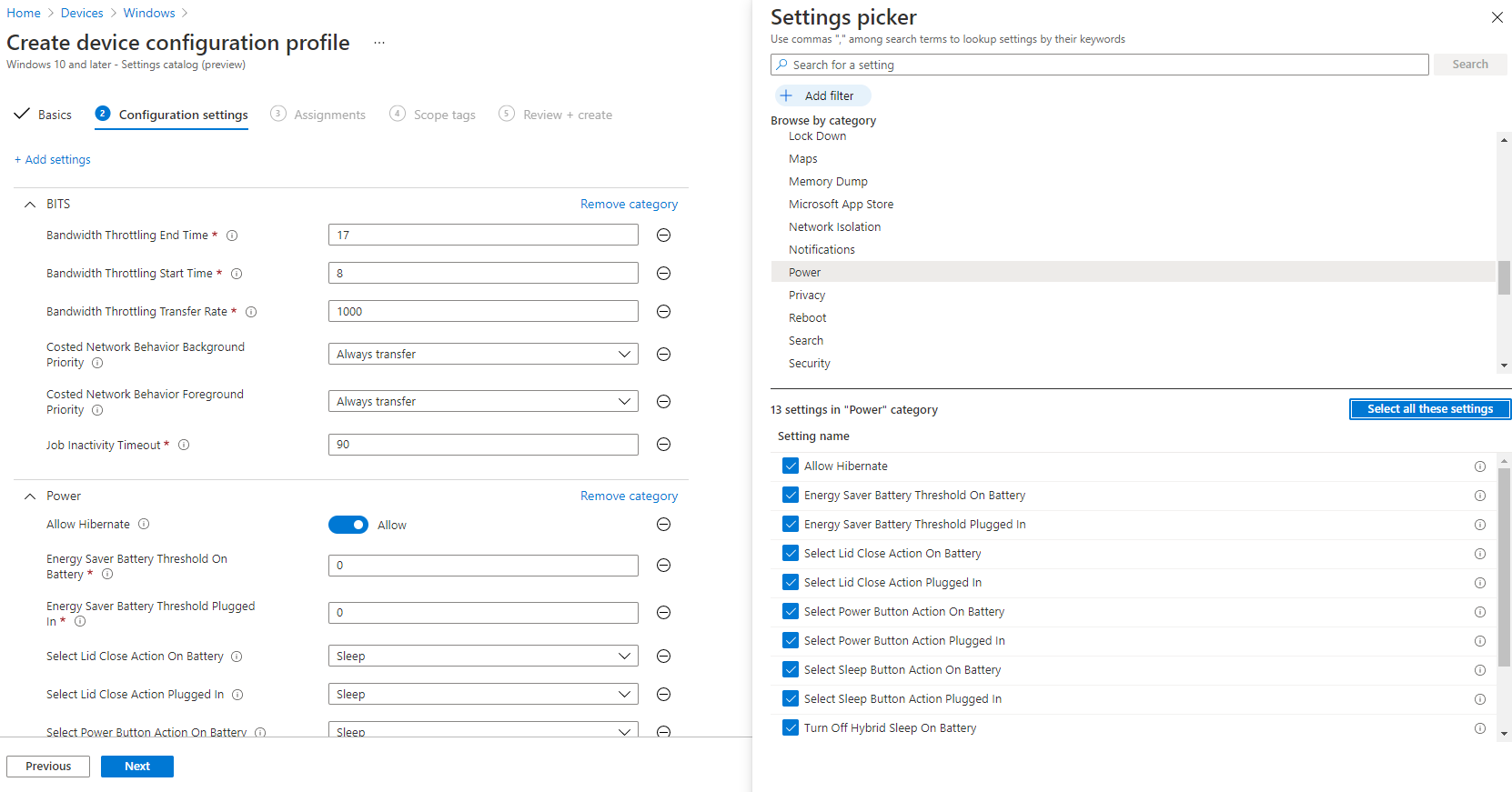
Other Policy Settings
Other areas such as the following;
- Background Intelligence Transfer Service
- Computer Restart
- Power Management
- Windows Updates
Defender/Endpoint Security Mapping
This section is actually less complicated to migrate over in the sense of that the sections for Endpoint Security settings are situated in one area when it comes to Intune. The policies for this in your On Premise MEMCM however can be somewhat spread but they are still close knit logically within the console it self.
So if we look into the Assets and Compliance - Endpoint Protection section in the MEMCM console we have the following categries;
- Antimalware Policies
- Bitlocker Management
- Windows Defender Firewall Policies
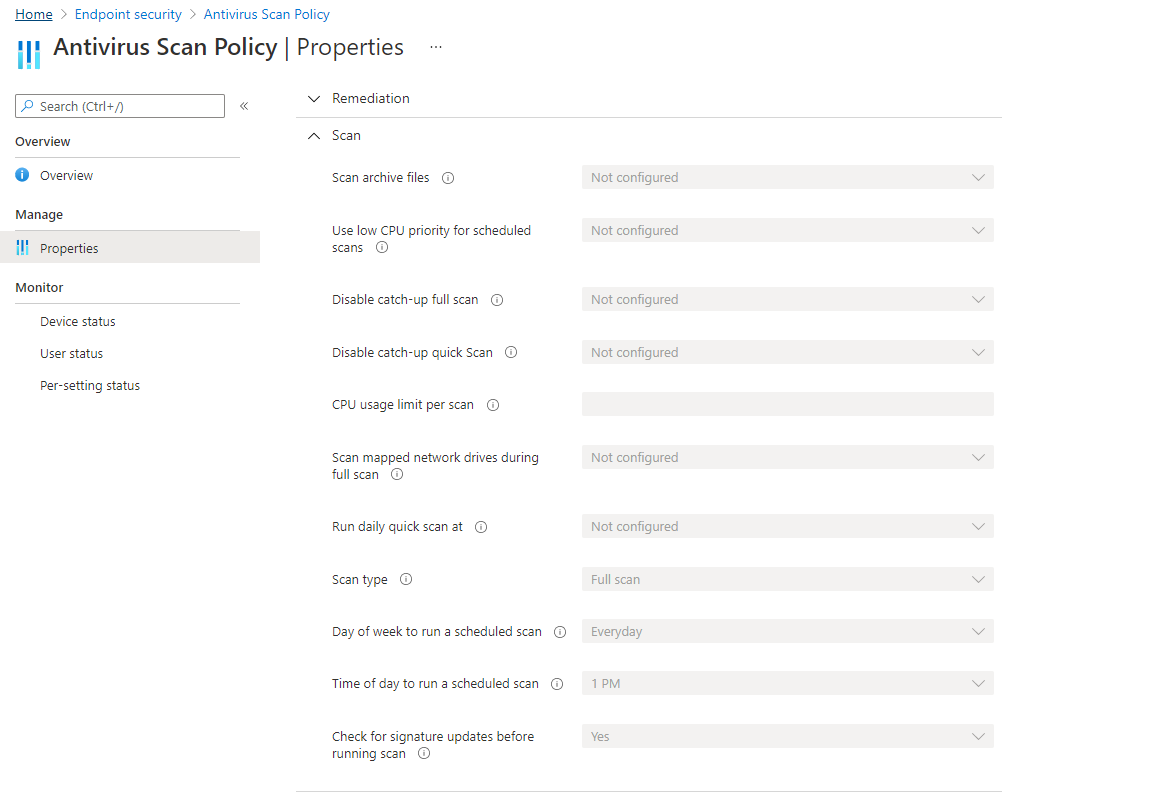
Antimalware Policies have the scheduled scan and scan details performed on each device with an agent, in this case we would migrate this into the EndPoint Security - AntiVirus Policies where we can dedicate settings specifically around scans, real time scanning.
As bitlocker was covered in the one of the earlier parts of the series this also has a straight forward migration mapping into the EndPoint Security - Disk Encryption Policies.
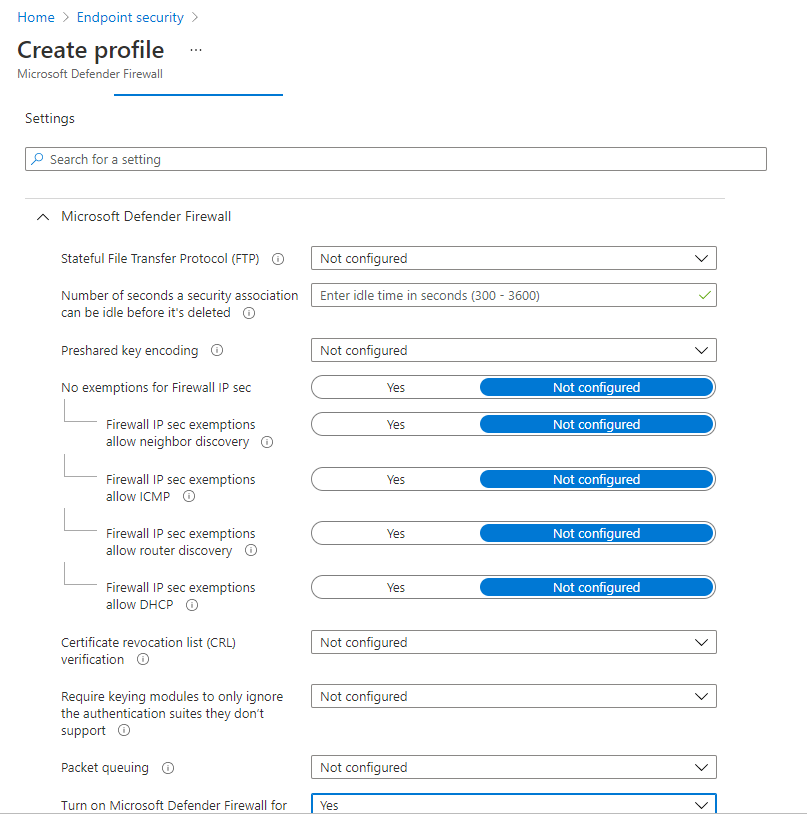
And for the Firewall Policies, whether you use these in the perspective of them being mainly controlled via MEMCM , or firewall policies which are controlled from a GPO level and distributed to all of your endpoints, these can also be mapped across to EndPoint Security - Firewall policies within Intune.
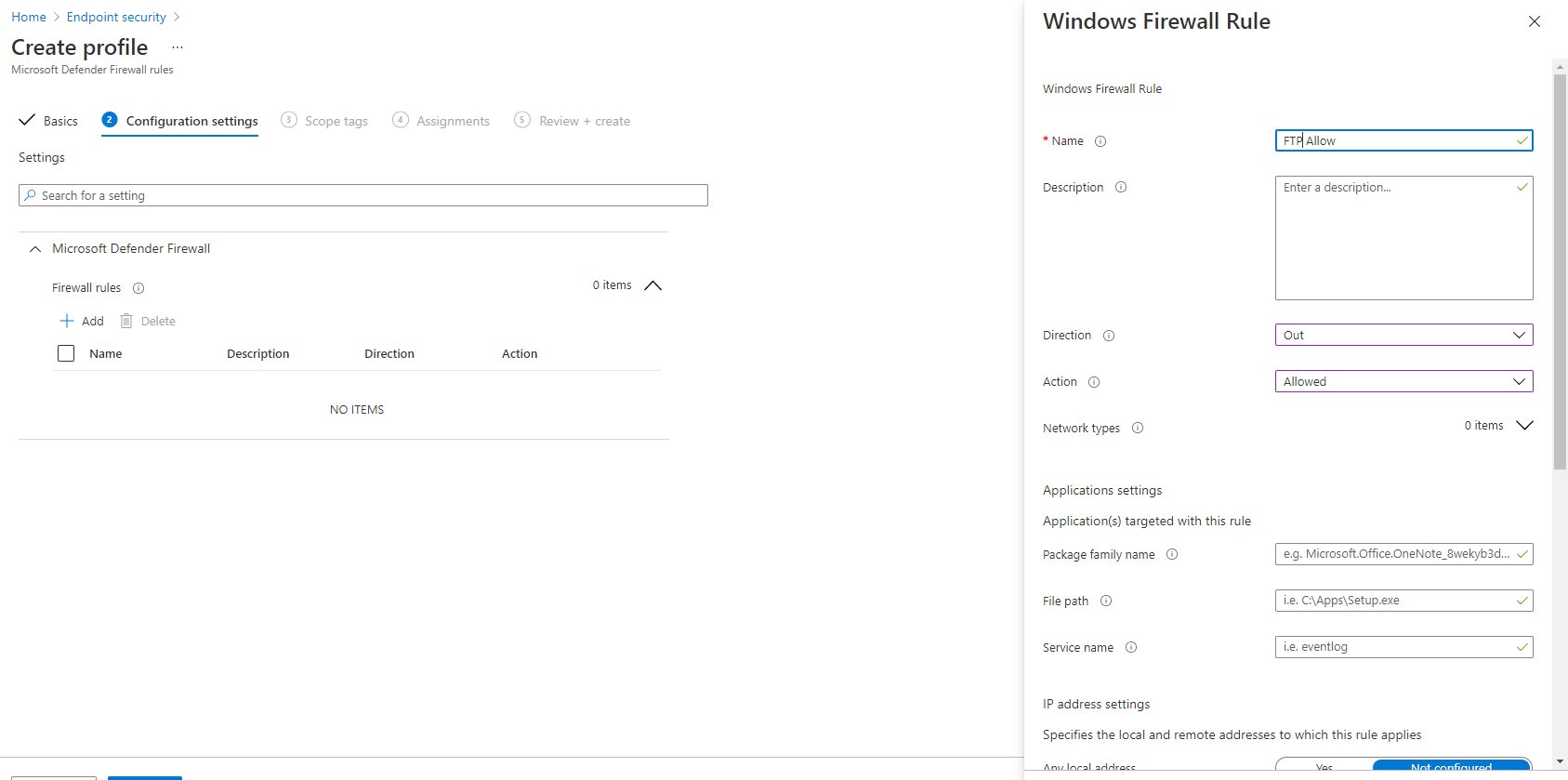
These are split up where you can define the settings for your actual firewall profile, and then another one specifically for firewall rules where you can configure the inbound and outbound traffic as seen below.
MDM Security Baselines
These baselines are set by default to add a foundational layer of security for all managed devices within Intune. Now where your policies are concerned within your On Premise MEMCM you may have some configurations which may either overlap, or perhaps be inconvenient to you where your other settings are concerned.
They provide a compliance standard for all devices globally within your Intune, so its best to proceed with caution when defining other policies within your Intune which may conflict with the security baselines.
Below is a screenshot of my MDM Security Baseline (December 2020) which is currently applied to all devices. Now as I have showed I had created a firewall policy it may not override this one, so if specific changes need to be made then you can change the distribution settings of where the security baseline has gone to if you want to build your own custom settings and baselines.
You do have the ability to create your own Security Baseline as well and define very similar settings which would be within policies which you are looking to migrate over into Intune. But please do so with care (Disclaimer at the top of the article)
End of the Series
Thanks again for looking through all six parts of this series and will be creating more around these areas soon which may give a more technical step by step approach on how to achieve these areas of migration.