MEMCM - Migration from On Premise to Intune Part 2 - Migration of Devices
Part 2 - Migration of Devices Planning
Introduction
This part is a continuation from the first part of this series which can be viewed here
This next part will be around how we will look at the migration of our devices from our current on-premise estate and into Intune, of course this will be very dependant on which scenario that you are facing which we will go into more detail on each one.
Scenario 1 - Windows 10 Endpoints only in the Estate
In a perfect world this is exactly where you would want to be with only just Windows 10 endpoints within your on-premise estate which will be the easiest form of transitions when it comes to the migration into Intune.
Having said that we need to analyse what is going to be the most efficient solution for this. We have the following options;
- Auto-Enroll Devices by AutoPilot
- Auto-Enroll Devices by Hybrid AD Join
- Manually Enroll Devices
So lets explore each of the options in which we have so that we can lay out the perfect option which is appropriate for your needs
( Note: Step by Step guides on how to perform each option will be coming soon)
Auto Enroll Devices by AutoPilot
Whilst we might be jumping the gun in terms of discussing the Auto Pilot process now it is quite applicable in this scenario as well when it comes to the process of auto enrolling devices.
Auto Pilot is not only just the process of on-boarding brand new machines which may or may not be sent to you from your hardware vendor, but it is used to automate the whole workflow of an automatic profile mapping which consolidates the process of an OOBE (Out of box Experience) for the user as well as the machine. This also is true within doing the same when it comes to auto-enrollment of devices too.
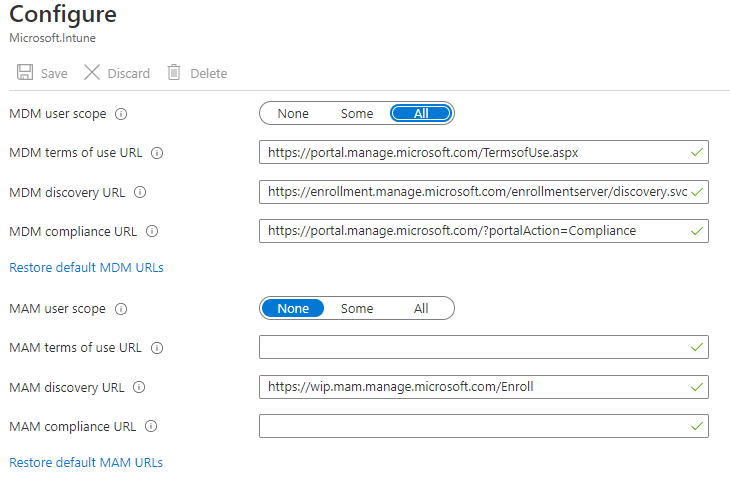
The main prerequisite of this is to of course have your Auto-Enrollment settings configured as seen below
Most tend to use all for the MDM user scope but using the "some" option is better if wanting to have more authoritative control on what or who is being enrolled into the estate.
With various steps in between the other major part is how we obtain the devices information to get them enrolled via AutoPilot and this is where the hardware hash information comes into play. These are the bits of information that are normally required when pre-staging AutoPilot devices before and when a user first logs in.
Auto-Enroll Devices with Hybrid Azure AD
This option is identical to the option above as it also utilises the whole AutoPilot process, however it differs due to this is an option if all of your machines are joined to an on-premise AD only, and having your machines then joined to an Azure Active Directory in an offline onboarding type of method in turn makes them hybrid joined machines.
In addition to the Auto-Enroll Settings you will also required something called an Intune Connector, which if you are familiar with how a Power BI On-Premise Gateway works then this is essentially the same in which it provides a gateway between your On-Premise managed machines and to the Intune Management in Azure.
Various more components come into play such as Domain Join profiles and also delegation configuration required on your on-premise Active Directory so that AutoPilot machines can be made/added to a container which you will specify which will essentially be owned by the machine you will decide to be your Intune Connector
( Note:
Server has to be at a minimum of Windows Server 2016)
Manually Enroll Devices
Assuming you don't have a huge estate then perhaps the manual way of enrolling a device could be more appropriate for many reasons. This process really involves you adding the machine to the enrollment of Intune Management by associating it to the user account which indeed has the correct Intune Administrator access to enroll it to Intune.
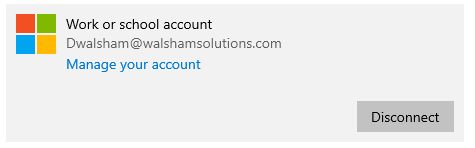
This is done through Work and School account access which I will detail the step by step on how to perform this.
- Do a search for "Access Work or School Account Settings"
- Click on the found option which should be found in System Settings
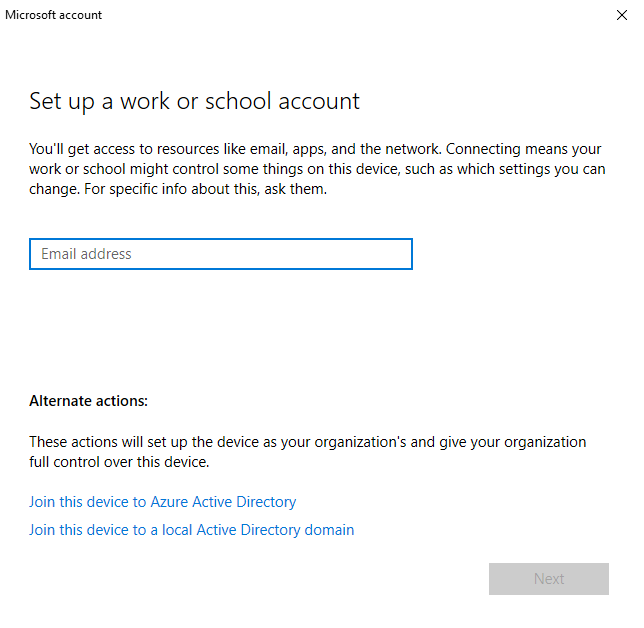
- Click the Connect option to get the following screen below
Here you can join your machine straight to your Azure Active Directory domain and then you will have the machine enrolled into Intune as an Azure AD Joined machine.
On the other hand you also have the option of enrolling the device only into Intune and not being Azure AD joined but this perhaps maybe beyond the scope of this article and also wouldn't recommend that option especially if wanting to have a fully migrated estate into Modern Workplace Management.
It's also worth pointing out that manually enrolled devices can also have an AutoPilot profile deployed to them which will allow them to be converted into AutoPilot devices so they can be overall managed by the whole AutoPilot process including the support of device resets to go into the whole OOBE process again.
Another method which can also be used is the Company Portal application which can be used to enroll your devices into Intune, though category wise they may show as a personal device rather than a corporate device which you would most likely get if the machine was Azure AD Join based.
The category itself can be manually selected but for auditing purposes it could be a good method of organising how devices are coming into your Modern Workplace Management.
Scenario 2 - Windows 10 & Windows 8.1 Devices
This scenario may capture a bigger audience than realised, as through many reasons and in the real world scenarios we still might have a mixture of legacy devices which would evolve around the Windows 8.1 devices and possibly as low as Windows 7 (sure hope not :) )
But in these situations there isn't really an option to migrate every single device into Intune as the rest of the estate will be more than likely left out of the migration
So in this scenario there are two options;
- Upgrade the machines to Windows 10
- Co-Management between On-Premise SCCM & Intune
Upgrade machines to Windows 10
This does sound like a no brainer :) but we do have to take into account there are a lot of estates which do have a good amount of legacy devices for many business reasons that they may perhaps play business critical roles and may not always be as simple as blowing those machines away.
But if wanting to move forward then at some point these would indeed need to be tackled, with another point of them being out of support as well.
Some Windows 8 devices can be managed by Intune if they either RT or sustaining mode but that's as far as it will go.
Co-Management Between On-Premise SCCM & Intune
Co-Management is the perfect blend to share the responsibility of device management between both Intune and SCCM. In this way your Windows 10 Endpoints can essentially be managed in Intune whilst the legacy based devices can be primarily looked after within the SCCM environment.
Another thing to take into account is the policy splits, as in if you are going to migrate your Windows 10 devices then you will need to have a form of replication in which the same coverage of policy compliance can be carried out through Intune the same way it had been successfully done through your on-premise SCCM Environment.
Co-Management works with nominating a collection which will contain the Windows 10 endpoints which you will use to be managed by Intune and SCCM, and these would also be online with an Azure AD group that also have the same machines synchronized within the Azure AD.
Scenario 3 - Windows 10 Devices and Mobile Devices
This is also another great scenario where we can bring all devices across for Intune Modern Workplace Management, especially when you have an MDM estate. Having said that just like Windows 10 needing to be on a minimum of build 1709 mobile devices also have its minimum requirements before they can also be managed by Intune
- Android Devices - 5.0 Minimum
- iOS Devices - 12.0 (13.0 for iPads) Minimum
- Mac OSX Devices - 10.13 Minimum
Also there are different options for enrollment for each device category.
- Android Enterprise
- Apple MDM Push
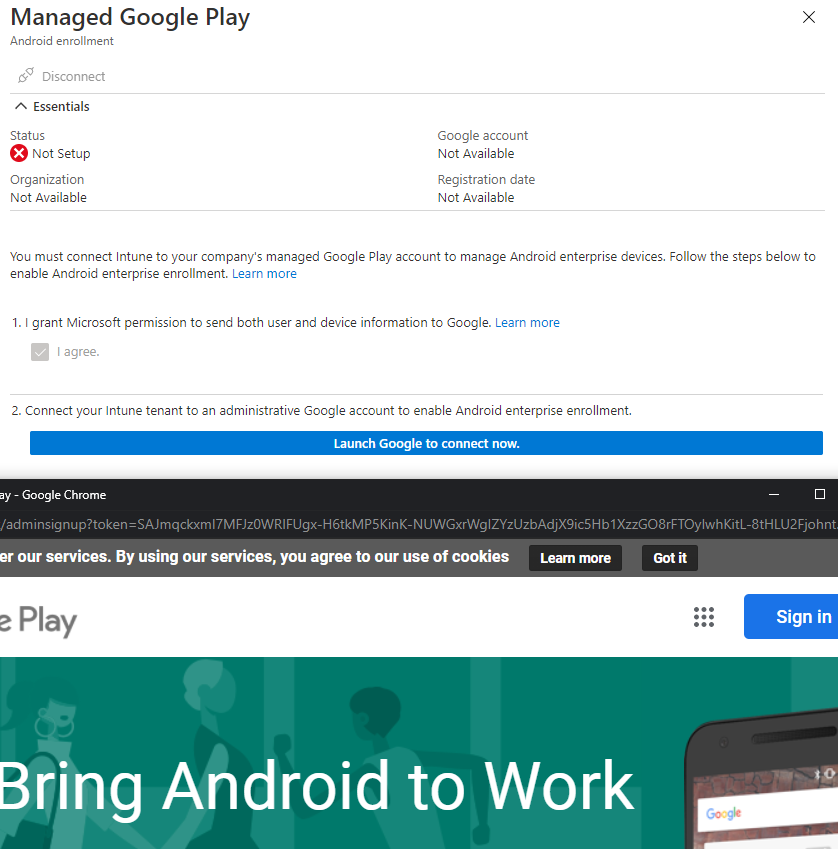
Android Enterprise
There are actually two ways in which you can enroll Android devices.
You can enroll devices by going through the Company Portal website which you can obtain from the google play store which is very similar to how you can enroll devices manually within the Windows Endpoints.
The other method is the Android Enterprise way which is also managed by google play. This is essentially where google play is managed by an email account which would be an Android Enterprise administrator account and this will be used where those mobile devices would also be signed into the Google play with the same email address and that would enroll your Android mobile devices into Intune.
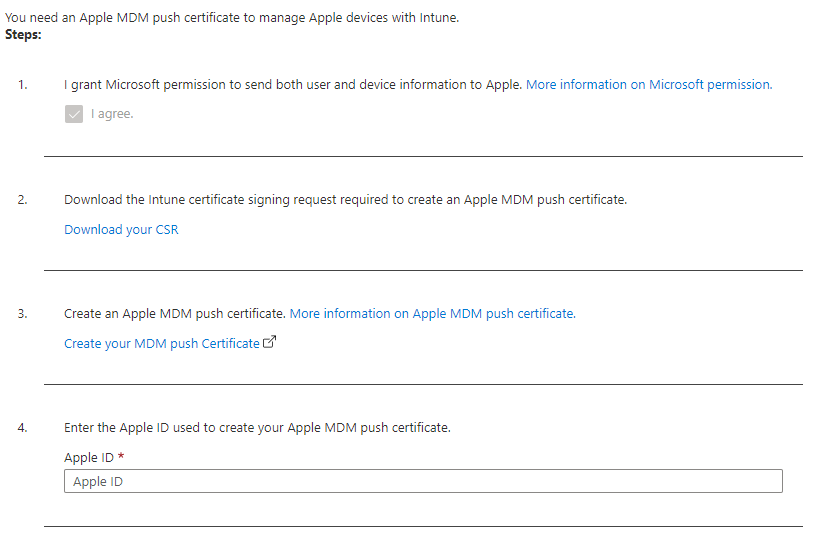
Apple MDM Push
With iOS and Mac OSX devices you won't be able to enroll devices into Intune using the Company portal way, as the main prerequisite requires an MDM push certificate which each device needs to have installed before it can be officially managed by Intune.
Similar to the Android Enterprise method you will require an Apple ID which would be the administrative email for which would be used to enroll the tenant into Intune.
Next Part
The next part we will look into the Software Library estate in preparation of how you would look at the planning of migration of various applications and types